What is Phishing?
The Angling Trust Describe Fishing – that’s with an ‘F’ – as a great way to get outside, spend time with the family, learn new skills and discover nature and generally speaking, as an honest, wholesome activity.
The UK National Cyber Security Centre (NCSC) define Phishing – that’s with a ‘PH’ – as an attempt to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malware, or direct them to a dodgy website.
Phishing is typically the impersonation of a person or brand and is an attackers’ most common entry point into your systems. Credential theft is their objective
Now, Phishing is not Malware, SPAM or Cross Site Scripting, although they often coincide.
Phishing is on the rise
Now there’s no doubt about it, there is more and more of this going on. Phishing is on the rise and it can only be because it is profitable for the criminal.
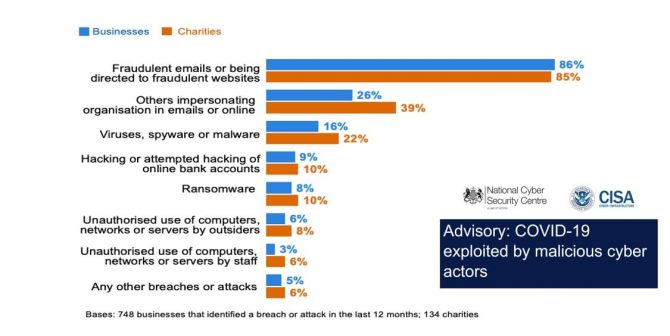
The UK Government Cyber Security Breaches Survey taken earlier this year commented that “The most common type of cyber attacks by far are phishing attacks – that is staff receiving fraudulent emails or being directed to fraudulent websites being “followed, to a much lesser extent, by impersonation and then viruses or other malware.
Phishing accounted for 45% of all incidents reported to the ICO in 2019.
Clear and present danger of phishing
- On average, it only takes 82 seconds from the time a phishing email is first distributed to the first victim being hooked. This highlights just how effective this type of attack is. For a limited amount of effort and cost, cybercriminals can quickly see results. (Source: Cyber Research Databank)
- Phishing accounted for 50 percent of all fraud attacks observed by RSA. Source: (RSA Quarterly Fraud Report – Q3 2018)
- 93 percent of data breaches are linked to phishing. (Source: Verizon’s 2018 Data Breach Investigation Report.)
- More than $9 billion has been stolen globally since 2015. (Source:FBI Internet Crime Complaint Centre (IC3).)
What does a phishing email look like?
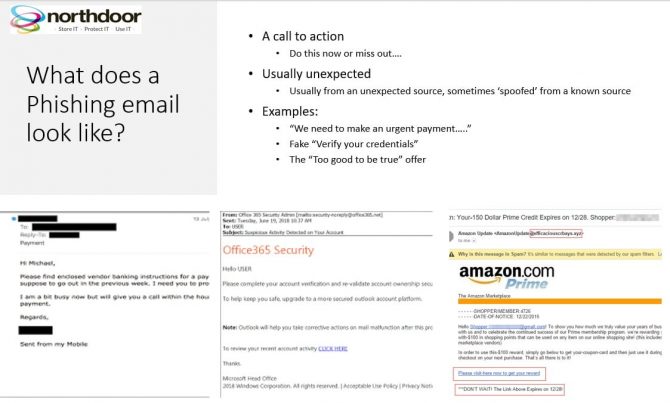
Now if, by chance, you have yet to see a Phishing email, they tend to have a recurring theme. Typically, there’s a call to action; an imperative. It’s usually an unexpected, yet plausible request or demand from an apparently credible source and sometimes from someone known to you. You see, an organisation or perhaps an authority figure can be spoofed. Here are some examples I found on the web.
On the left is a request to make an urgent payment, addressed to the recipient. This is the direct approach; it will come from someone you know and will be spoofed. In the middle is a very credible looking, yet falsified password reset request. This isn’t particularly targeted and will be broadcast – someone out there will have just such an account. The third item is firmly in the too good to be true category. Click here for a very, very special offer…..
How can companies reduce the risk?
Education is a critical element and prepares a first line of defence (and most often weakest defensive link) – the employee. Many anti-virus and other packages including phishing simulations with sample campaigns. The NCSC has issued guidelines as a series of ‘layers; to prevent an attack. Layer 1 essentially says find something beyond simple education to assist the defence.
Many people, often senior employees, think that only more junior or ‘less intelligent’ staff members are going to get tricked by phishing attacks. Frankly, why take the chance?
The very nature of phishing attacks means that they are designed to appear credible and consequently no one can take the threat lightly. Criminals target specific roles within an organisation or even specific individuals, launching an attack when that person is most likely to be off their guard. This highlights why attacks have increased so much over the last few months in the face of the global pandemic and says a great deal about the character and nature of most of the criminals involved.
Reducing the risk

Introducing innovative technology to help combat the threat
Some companies are no longer taking a risk on the ‘intelligence’ or savviness of their employees and are implementing proactive defences against a constantly moving enemy.
To turn the tide against cyber criminals, it is vital to shift the burden of cost and complexity onto the attacker. The latest advances in artificial intelligence (AI) and machine learning are now allowing IT departments to do exactly that.
AI can help organisations stop phishing attacks in their tracks. Using linguistic and technical analytics algorithms, AI solutions can help identify signs of compromise with pinpoint precision. Such solutions can re-write suspect emails to disable questionable links and add user-friendly warning banners to highlight possible phishing emails to employees; thus, helping them to make informed decisions as to what they do or do not click on.
Crucially, the key to AI is that it is always learning. Without intervention from IT personnel, AI solutions can become more accurate over time which means that it is always one step ahead of new email phishing tactics – a complete reverse of the current situation. As a result, the IT team can focus on other, value-added activities, while the business can be confident that legitimate emails will reach without delay.
Those companies that continue to ignore the threat of phishing attacks and rely instead on employees correctly identifying and dealing with potentially dangerous emails, will at one point, inevitably become a victim. However, innovative, AI technology will allow companies to not only more effectively take on the phishing threat, but take the pressure off employees, whilst freeing up the IT department to engage in other key areas of the business.